Project Information
Type: Cloud Security / Automation / Forensics
Stack: AWS IAM, GuardDuty, Lambda, CloudTrail, S3, EventBridge, Terraform
Project Summary
This project simulates an IAM compromise in an AWS environment and implements a fully automated incident response workflow, including detection, containment, forensic evidence collection, and security team notification.
Challenges
- Late detection of IAM compromises
- Slow and error-prone manual responses
- Lack of traceability and forensic evidence after incidents
Architecture & Solution
Amazon GuardDuty detects suspicious IAM behavior and triggers an EventBridge event. An AWS Lambda function automatically isolates the compromised identity, disables access keys, collects CloudTrail logs, and sends alerts to the security team.
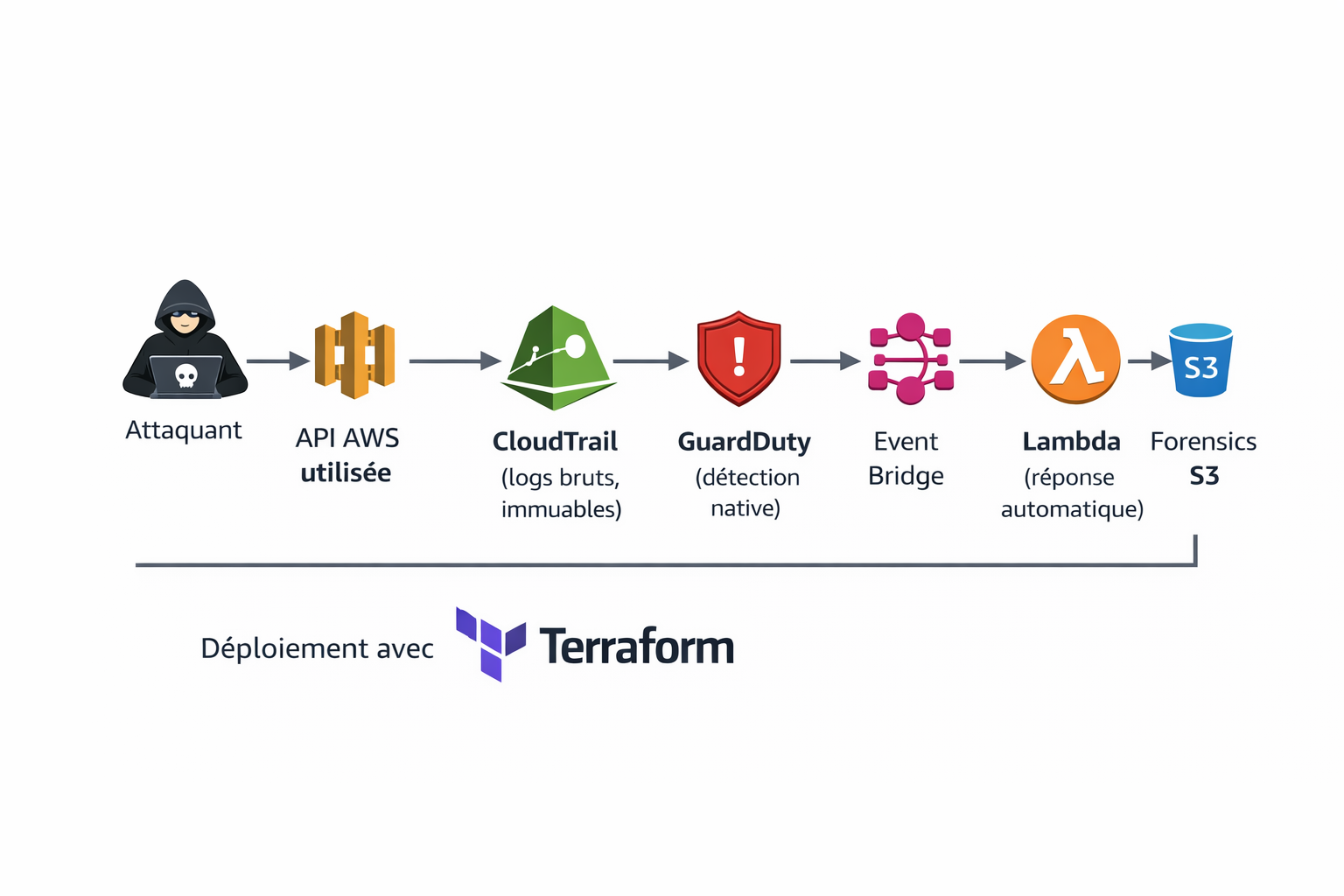
Incident Response Workflow
- Automatic detection via Amazon GuardDuty
- EventBridge rule execution
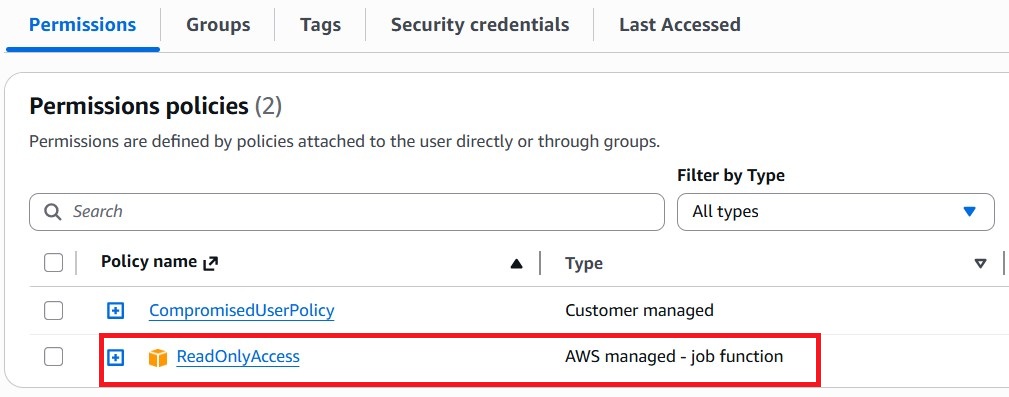
- Disabling compromised IAM access keys
- Applying a temporary restrictive IAM policy
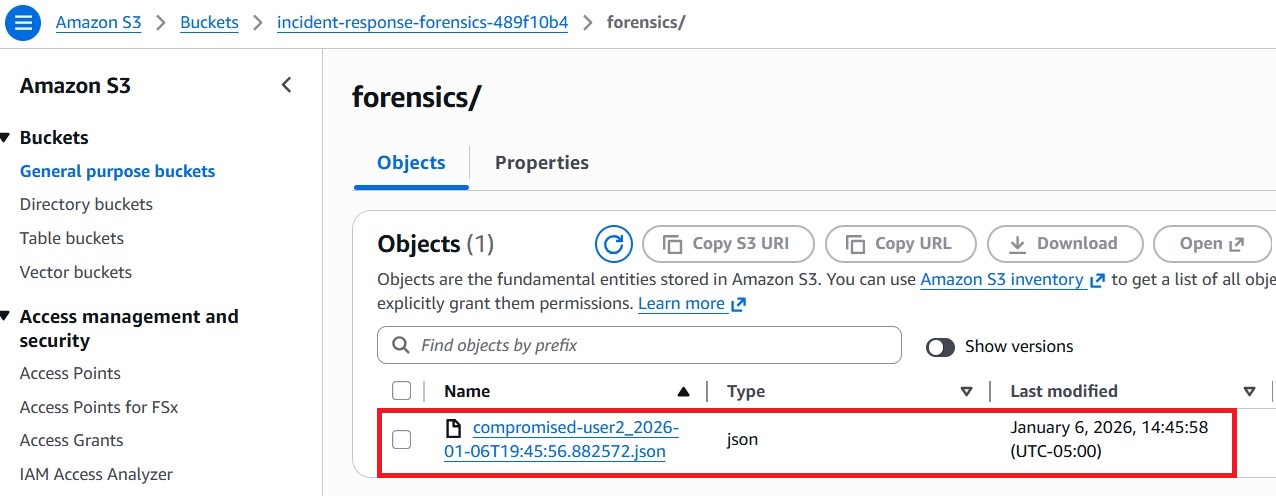
- Collecting CloudTrail logs in a secure S3 bucket
- Notifying the security team via SNS
Results
- Incident response time reduced to seconds
- Immediate isolation of compromised identities
- Centralized and secure forensic evidence
- Reusable architecture for other incidents (S3, EC2)